The U.S. National Security Agency has figured out how to hide spying software deep within hard drives made by Western Digital, Seagate, Toshiba and other top manufacturers, giving the agency the means to eavesdrop on the majority of the world’s computers…
That long-sought and closely guarded ability was part of a cluster of spying programs discovered by Kaspersky Lab, the Moscow-based security software maker that has exposed a series of Western cyberespionage operations.
Kaspersky said it found personal computers in 30 countries infected with one or more of the spying programs, with the most infections seen in Iran, followed by Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. The targets included government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists, Kaspersky said.
The firm declined to publicly name the country behind the spying campaign, but said it was closely linked to Stuxnet, the NSA-led cyberweapon that was used to attack Iran’s uranium enrichment facility. The NSA is the agency responsible for gathering electronic intelligence on behalf of the United States.
A former NSA employee told Reuters that Kaspersky’s analysis was correct, and that people still in the intelligence agency valued these spying programs as highly as Stuxnet. Another former intelligence operative confirmed that the NSA had developed the prized technique of concealing spyware in hard drives, but said he did not know which spy efforts relied on it.
Kaspersky published the technical details of its research on Monday, which should help infected institutions detect the spying programs, some of which trace back as far as 2001.
Another opportunity to confirm which politicians and pundits are serious about protecting individual privacy and which consider kissing government spy-butts more important. Let’s see who lines up on which side in coming days discussing this latest revelation.

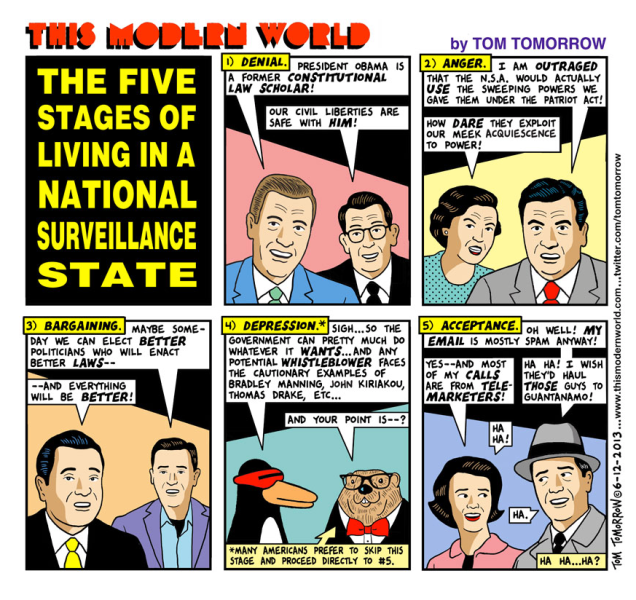














Oh the sheeple…..
Stage 6) JOIN ‘EM
“Actually, I hear surveillance work pays pretty good! Where can I sign-up?”
This message brought to you by the people who post all their crap on Facebook.
Wallow in the ignorance — you’ll feel better. Trust me! The truth is something you will deny anyway.
The article provides the solution:
We need to be able to see the source code of the software/firmware that’s running on our devices, and make sure there are no “back doors”. It’s tough with hard drive firmware (or BIOS code for that matter) but that’s really the only way we can be sure the software isn’t compromised.
Of course, who knows what back doors might lurk in the hardware itself… :/
The solution is to have more software written not by Americans. That will eliminate the need for H1Bs as well, as all software jobs go overseas.
If it’s software running in American banks, I’d think they would want it written by Americans. Just like the Chinese want their software written by Chinese.
Be wary of free software, particularly password managers, written by companies in other countries.
In my past I worked on US Government projects for Raytheon, with a security clearance I can’t tell you about. Occasionally people from other countries came through. We were told to be particularly wary of the French and the Israelis. Those two groups had a reputation for industrial espionage against their allies. I would personally not use software written by a company based in either of those countries.
Just be aware… of course, companies based in the US can screw you too. :/
Now, I wouldn’t mind the Government intruding into my system quite so much if I could call them to recover the spreadsheets and documents I accidentally deleted.
If it’s Hillary vs Rand Paul, for whom do you vote?
Rand Paul.
Not likely to come up with a liberal moderator or the main stream media: http://thefederalist.com/2015/02/18/13-foreign-policy-questions-for-hillary-clinton/
I guess according to this cartoon, this is a non-issue with racial minorities.
I can’t see how this would work. Any form of spyware has to be executed for it to work. Most people delete partitions, and format and re-partition new HDDs and would clear out bullshit like this before they use it. In fact if you do have any sort of malware, even on the MBR, you do exactly this to clear the drive out… Short of a low-level format, which most people don’t do anymore (people do zero-write drives not the same as low-level).
So maybe this spyware is in the firmware of the drive? What if you use the drive with a non-windows OS? How can a HDD send information over the internet on it’s own when it cant possibly have access to the internet?
Cloud storage is a much easier target to “Spy” on.